Posted in 2015
What is Privacy?
Over the past couple of years, “privacy” has received widespread media coverage. Some people say that if one does not have anything to hide, then there is no need of privacy. A lot has been written about the amount and kind of data collected by corporations. It is said that there is no need to worry as only metadata is collected and not the data itself. What it really means is that, users have lower level of protection by law as compared to a situation where data is being collected. In an earlier article here I have written how metadata can sometimes provide more information than the data itself. But what is “privacy”?
The first legal article on privacy titled “The Right to Privacy” was published in 1890 by Samuel Warren and Louis Brandeis. In this article they discuss privacy as the “right to be let alone”. They also mention “Numerous mechanical devices threaten to make good the prediction that ‘what is whispered in the closer shall be proclaimed from the house tops.’” In the same year William James addressed the idea of being able to present ourselves to different people by withholding private information.
Another way of looking at privacy is by using the metaphor used by Erving Goffman in his book “The Presentation of self in Everyday Life”. He writes that society is a stage in which we are actors. But as with most stages, there is a backstage, an area which is invisible to the public, where we do things not to be presented to the public. Privacy plays the role of allowing us to prepare for the presentation before going on to the stage.
Stephen B. Wicker mentions that privacy could be thought in terms of observability and controllability in control theory. Controllability denotes acquiring enough information so that the system can be driven to the desired state. An example would be personalized advertisement. If the advertiser has enough information about the person, then the advertisements viewed by the person would be suited to the needs and the advertiser would reap benefits.
In 2009, Helen Nissenbaum wrote a book “Privacy in Context” in which she introduces the idea of contextual integrity. She maintains that we control the personal information we want to hold by having a boundary. In addition she uses the metaphor of a zone of seclusion, in which the control is handled differently depending on the context and the person’s perception of solitude. This includes that the person is able to exercise various thoughts without worrying of censure.
Post-Quantum public key cryptosystems
Public-key cryptosystems, such as RSA, Diffie-Hellman and Elliptic Curves, which are in use today are based on Integer Factorization Problem (IFP) or Discrete Log problem (DLP). Their strength lies in the difficulty of determining the private key when the public key is known. These algorithms are part of internet standards, for example TLS and GPG, and are used for key exchange. But these algorithms can potentially be broken in polynomial time by Shor’s algorithm if quantum computers become operational. This means we need to look for cryptosystems which will not be susceptible when attacked using quantum computers.
In 1978, two years after the publication of the seminal paper by Diffie and Hellman on the use of private and public keys for cryptography, McEliece proposed a public key cryptosystem based on algebraic coding theory. In this system, a generator matrix is used as the private key and a transformed version of it as the public key. The security of the system lies in the hardness of decoding a large linear code with no visible structure. An attacker would is forced to use syndrome decoding while the person in possession of the private key could use fast decoding algorithms. The original McEliece cryptosystem, based on binary Goppa codes, has not yet been broken in polynomial time. The main advantage of this system is the fast encryption and decryption mechanism, which is two or three magnitude faster than RSA. One might wonder why this algorithm has not found widespread implementation yet. There are two disadvantages which are the main reasons for the lack of popularity of this system. First, the key size is very large and second, information rate is very low (k/n = 0.5, which means there are as many redundancy bits as information bits). This increases the bandwidth required which makes the system prone to transmission errors. The original system required public keys of size in the order of hundreds of kilobits while RSA uses a key size of 1024, 2048 and 4096 bits.
Researchers have been working to reduce the key size of the McEliece cryptosystem so that it can be used in practical applications. To reduce the key size many alternatives to Goppa codes have been proposed. One such alternative is based on Low Density Parity Check (LDPC) codes. Though it seemed to be an attractive alternative, it was possible to search for low weight codewords in the dual of the public key. In order to counter this weakness the use of Quasi-Cyclic LDPC codes has been proposed. QC-LDPC is an effective alternative to reduce the size of public keys of McEliece cryptosystem. This system requires a public key of size about 50 kilobits to achieve a security equivalent of 2048 bit RSA. This is a reduction of key size by a magnitude of ten from the original McEliece cryptosystem while maintaining the advantage of fast encoding and decoding.
Extended Mind
One of the most popular dualism is the substance dualism introduced by Rene Descartes. Descartes distinguished the mind from matter and claimed that they are fundamentally different. He describes the mind as a thinking substance and matter as an extended substance. If matter and mind are different substances, is there a boundary for the mind? It is a common notion that the mind is nothing more than the working of the brain which resides in the skull. Hence the mind is in the skull.
Andy Clark and David Chalmers, in their seminal work ‘Extended Mind’ in 1998, claim that cognition is not restricted to the head but can be extended using different artifacts. This challenges the view that the mind is a little black box in the head. The basic idea of ‘Extended Mind’ is that the mind is not constituted just by the brain but also by electronic devices, papers and other items which are outside the head. The location of the mind is irrelevant. It is the functionality that is considered here. It doesn’t matter if the calculation is performed in the head or using a calculator.
Technology has become an integral part of who human beings are. Technology doesn’t just play a passive role but instead influences decisions. There is certain sense of dependency on books, computers and calendars. If a person spends a large part of the day with their mobile phone, to make calls, find routes to new places, read news articles, etc. is the mobile phone part of the person’s mind or is it still just an external device? Would the mental state of the person change is the mobile phone is broken or switched off?
Even if all the electronic devices and papers are wiped out of the surface of the earth, aren’t humans influenced by their fellow beings and dependent on them? Clark and Chalmers question, “And what about socially-extended cognition? Could my mental states be partly constituted by the states of other thinkers? We see no reason why not, in principle.” Conversations often involve ‘Remind me to send X to Y’. How different is this from setting reminders on the mobile phone? How different is it to remembering in the head? Aren’t these complimentary?
Image Source: https://xkcd.com/903/
Implicit dualism
It can be commonly observed that human beings, with few exceptions, have a dualistic way of thinking and speaking. According to Aristotelian logic it has to be either true or false. But should it be the case? Dualism could be explicit but it could also be implicit. How would you answer the above question about logic? Yes or No or both?
Dualism implicitly creeps into speech. For example ‘It is a sunny day’, ‘This statement is false’, etc. The listener seems to be left in the position of agreeing or disagreeing. On closer inspection it can be observed that both statements contain the word ‘is’. The first example ‘It is a sunny day’ could be considered dualistic. But what if it is intermittently raining throughout the day though sunshine makes its presence felt for most part of the day. Can it not be both a rainy and sunny day? Can the truth not be restricted to just two boxes?
The second example ‘This statement is false’ appears paradoxical. If it is true that the sentence is false, then it contradicts itself. If it has to be true that it is false that it is true that it is false and so on. How can this contradiction be solved by Aristotelian logic? One possible way would be to restate the sentences in E-prime (a prescriptive version of English language which excludes all forms of ‘to be’).
The use of E-prime can be critical in some situations. If a person is witness to a hit and run accident, he/she could state ‘The car involved in the accident was a black Hummer’ or in E-prime ‘The car involved in the accident appeared to be a black Hummer.’ The former statement gives an impression of surety and absolute which might not be the case. The latter statement is not absolute and informs the listener that the colour and make of the car were as interpreted and remembered.
E-prime appears to be just one way to make thoughts and speech more flexible and less dualistic.
Penrose Stairs Image Source: http://r-boisard.deviantart.com/art/Penrose-stair-243885764
Data about data
“Metadata absolutely tells you everything about somebody’s life. If you have enough metadata you don’t really need content.”
-Stewart Baker
Many people do not feel safe when they know that another entity is collecting information about them. If an individual collects information about you and uses this data to follow you, then it is called stalking. But if an organization wants to collect information about you and millions of others, often it is tagged as security measure. Organizations require a lot of storage space to store data. Earlier the storage space used to be in the form of large rooms filled with papers, now it is in the form of hard drives. With increasing amount of data about each person, organizations which want to store data realized that they will run out of space or will need to spend more to add space. They had to come up with a way to store information in limited space.
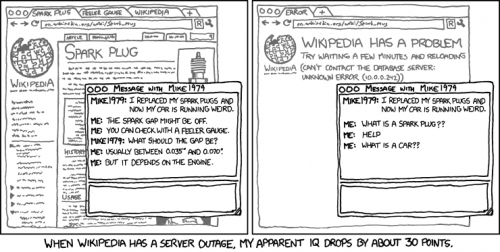
Individuals who care for their privacy might be relieved that organizations may after all not collect data about them. But this is where metadata enters the picture. Metadata is data about data. For example, data would be the recording of a phone call Bob made to Alice while the metadata would include the time of call, duration of call, location of your phone, location of your friends phone and of course both your phone numbers and name. Storing a phone call would require many megabytes of space while the metadata requires only few kilobytes of space. Many might question, what organizations can do with phone metadata without knowing the contents of the call.
Phone metadata provides organizations with enough information to map the life of people. Your location is recorded in order to provide continuous connectivity. The user does not need to make calls in order to give away their location. Now assume the organization only collects the location metadata of hundreds of users, it can trace the movement of people and basically draw a map. Looking at the overlapping location of multiple users at a particular time, it can be known with high probability that this group of users are associated with each other. If the location happens to be a football stadium owned by the local club, and the same group of users’ meet at the place every time there is a game being played, it can be known that they are followers of this particular club. Note that the users did not voluntarily mention about their favourite football club. But it was known just by tracking their location. This is a trivial example with only one kind of metadata. So much more can be known if other types of metadata such as online search terms are also known by the organization.
A lot of people would not mind letting others know of their favourite football club. But let us say that two people are in an intimate relationship and want to keep it a secret. They call each other often late in the night. The call duration is often more than an hour long. But after few months, the duration of calls reduces and after few more months the frequency of calls also becomes irregular. Using this kind of metadata, it can be assumed that there was a relationship between these two people which has ended. When there is metadata, who needs data?
A Wealth of Information
“A Wealth of information creates a poverty of attention”
– Herbert Simon
In some parts of the world, it is assumed that most people who want and can afford, have access to the internet. I see advertisements saying “Rent includes internet. Who lives without internet these days?” I would say that the person who has placed the advertisement is living in a bubble. But does this person need to know about everything in the world? Over the past couple of years hundreds of Exabyte’s of information has been added.
Let us say that you are one of those who has the urge to know a little of everything that is happening in this world. You access news articles daily, probably watch news on television, read variety of books, follow “important” personalities on twitter, regularly check your emails, instant messages, watch new and old movies and search for other information on “popular” search engines. You are flooded with spam mails and advertisements as well. How much of this information do you need? What is the signal-to noise ratio? In addition you may not realise that you are living in a “filter bubble”.
Information pollution has an impact on individuals, businesses and society at large. But how can you reduce the impact of information pollution? Until unless you have read a book or watched a movie you don’t know if it is useful to you or not. Many corporations restrict usage of social media access of their employees during working hours. The question arises, why does anyone want to access social media sites while working? This is one example of continuous partial attention (CPA), in which a person is simultaneously paying attention to multiple information sources. Often it is an automatic process due to habit and not a conscious one.
The concept of attention economy discusses the abundance of information and how its immediate availability limits the human ability to process the information. This has lead to corporations incorporating intangibles such as personalization, ease of access and immediacy to attract consumers as reproduction of information does not cost anything.
In this ocean of information, how much is enough?
Education
“Education is the ability to listen to almost anything without losing your temper or your self-confidence.”
-Robert Frost
During one of the discussions I had during high school, I was asked if the knowledge gained through books and what we study in order to obtain a degree are what I would call education? As a sixteen year old who had not thought enough about education, but rather been ‘part of a system’, I was convinced that my answer was NO.
Over the past few years my belief in my answer that day has only grown stronger. I still may not be able to define what education is and I am not sure if I want to either. But it is certainly more than just obtaining multiple degrees. This does not mean that I disregard University education. University education has its own value in the current system and certainly provides a good foundation for people to fall back on. But I think education is less about teaching and more about learning and living. Learning from different sources about different things and entities, incorporating them, forming perspectives, acknowledging that others can have different opinions and have the ability to discuss peacefully and finally be willing to change if need be. It is not about knowing everything but about having a sense of curiosity. In short education is to live and let live.
I think, the TU being a technical university, has made an effort to allow students to look beyond the realms of their university degree. Studium Generale is one such organization in the University which provides opportunity for students. In the form of VOX and SG Academy, students have the opportunity to think and share their opinions without having the necessity to be right or correct and also listen to other’s perspective and have a fruitful discussion.
There are so many simple things that we overlook in our daily lives. These are often questions that are discussed in SG Academy. One such question is What is the relationship between math and reality? Mathematics plays an important role in our lives and yet it is considered that a common man has no knowledge of a major chunk of theoretical Mathematics. But why does mathematics play a vital role in our lives even though we are so often ignorant of the principles involved in our daily activities? Do we need to know it all? Is it any different from so many languages which have symbols that have a specific meaning?
Join the dance
“The only way to make sense out of change is to plunge into it, move with it, and join the dance.”
― Alan W. Watts
In March, I had the opportunity to visit the theater in Delft (Theatre de Veste). I watched the three dance routines choreographed by David Middendorp. All of them had an element of technology attached to them.
The first routine was ‘Three Rooms’ and was my favourite. In this routine, two dancers were involved and one could see them being pulled and pushed by elements from outside the room in view. The dancers first oppose, then surrender and finally get carried away by the external elements. This was an abstract routine and left the interpretation to the observer. The first stage of opposition gave an illusion of three rooms being involved. One room that was depicted on stage. The other two on the two sides of the stage from whose inhabitants or other elements prevented the dancers from entering. As the routine progressed, and the reaction of the dancers to the push and pull changed, one realises that there is just one room. It is the mind of the observer that creates the illusion. One might wonder what element of technology was used here. The choreographer, David, was a dancer but he doesn’t dance anymore. So he choreographs by using a mobile app and drawing lines and curves on it which act as a cue for the performers.
The second routine was ‘A dark Flirt with Gravity’ in which the dancers interact with the drones during the performance. The idea is to depict the co-existence of technology and humans and depict the positive and negative effects of technology on the society. The third routine was ‘Blue Journey’ which depicts a struggle of a girl with herself and with the world. She has a blue shadow and realizes that she is different from others around her. We see how she and the society deal with her shadow.
Privacy and security
“Privacy and security are those things you give up when you show the world what makes you extraordinary.”
-Margaret Cho
Quarter 3 has been filled with courses that have assignments and projects. I have opted for five courses which are from diverse fields. Couple of them are from the signal processing field and couple of them are security related while the last one is Medical Imaging.
Estimation and Detection course is compulsory for students of Signals and Systems track. In this course the theoretical background for estimation was dealt in detail while we also had few lectures on detection. The theory is widely used in many present day applications such as radar, sonar, speech enhancement, communication systems, etc. This course is useful for students who are interested in taking Signal Processing for communication course in Q4. Distributed Signal processing course included few concepts in convex optimization as well as graphical models. Both these topics were dealt with keeping Distributed systems in mind.
Network Security and Hacking Lab are the most interesting courses for me this quarter. In Network Security course, vulnerabilities at each of the OSI layers was discussed along with possible countermeasures. The homeworks included implementation of known attacks at the Data Link and Network layer. Though the homeworks were time consuming, it helped in understanding the security requirements of the network stack better.
Medical Imaging course offered by EWI includes Computer Tomography (CT), Magnetic Resonance Imaging (MRI) and Acoustic Imaging. The lectures included a brief overview of the concepts in of these topics. The course grade depends on different assignments for each of these topics. The assignments include a CT image simulation using Matlab, a review on a paper on MRI and a design project for Acoustic Imaging.
In February, Vox Delft screened the movie ‘My Dinner with Andre’. The movie is philosophical and involved two characters who are involved in an extended conversation about life. In addition, Vox Delft also had discussions on couple of interesting topics such as ‘What is there was no such thing as reality?’ and ‘What are the biggest dividing forces in the world?’ I volunteered for TedXDelft which was organized on February 27th. I had the opportunity to have engaging conversations with speakers as well as guests.
Image Source : http://en.wikipedia.org/wiki/Security_awareness#/media/File:Loose_Chips_Sink_Ships.jpg
Information is the oxygen of the modern age…
“Information is the oxygen of the modern age. It seeps through the walls topped by barbed wire, it wafts across the electrified borders.”
— Ronald Reagan
After quarter 2 exams concluded in the last week of January, there were no lectures for a week. There was snow in the weekend after the exams followed by the sun shining brightly for a couple of days. The week off gave me time to read few interesting articles. In this blogpost I will mention few interesting activities that I was involved in during the exam weeks and the week after.
On the afternoon of January 26, Delft Data Science (DDS) New Year event was organized. The event included presentations, masterclasses, posters as well as an interactive panel discussion. The initial presentation gave a brief overview of the “Foundation of Data Analytics and Cyber Security” in TU Delft. Two research directions – Cyber Security through Big Data and Securing Big Data- were addressed briefly. Then the following three masterclasses were conducted:
1. Security and Privacy: Conflict or Harmony
2. Why have a lock at all? On the fallacy of ICT Security
3. Botnets: The Challenge of Bot Detection
As the masterclasses were conducted parallelly, one could attend only one of them. More details on the Masterclasses can be found here. The masterclasses were followed by a lecture on “Anonymizing Darknets”. The lecture was given by Martijn Spitters from TNO and he gave a brief overview of the kind of activities for which darknets are predominantly used. The next lecture was given by Gerald Friedland on “Content-based Privacy for Consumer Produced Multimedia.” You can watch his lecture on collegerama. The event was concluded by an interactive panel discussion wherein few specific questions were discussed.
The video below was part of Gerald Friedland’s talk and certainly requires you to watch.
On January 27, VOX had a discussion on the topic “Can we get over Territorialism” and on February 3, “What if there is no reality” was discussed. You can find out more about VOX here.